Table of contents
Let’s face it: the cybersecurity world can feel overwhelming. You’re expected to be some mix of a wizard and a code ninja, wielding tools like magic spells to ward off digital evildoers. But here’s the good news – some of the most powerful tools in the cybersecurity universe are completely free. Yep, you heard me right. No credit card, no subscription, just pure, unadulterated cyber power. Let’s dive into eight must-know tools that every aspiring cybersecurity enthusiast should have in their arsenal.
1. Wireshark: The Sherlock Holmes of Network Analysis
What it does: Wireshark is the ultimate network protocol analyzer, a powerful tool that allows you to capture and examine data packets moving through your network. By using Wireshark, you can dissect these packets like a digital forensic scientist, gaining insights into network traffic, identifying potential issues, and understanding the flow of data. This makes it an invaluable resource for troubleshooting network problems and ensuring security.
Why it’s awesome: Wireshark allows you to monitor your network in real-time, giving you a clear view of all activities. If you're curious whether someone is using your bandwidth without permission or if your computer is connecting to a suspicious IP address in a far-off place like Siberia, Wireshark can help you uncover these issues. It provides detailed insights into your network traffic, making it an essential tool for maintaining security and ensuring everything is running smoothly.
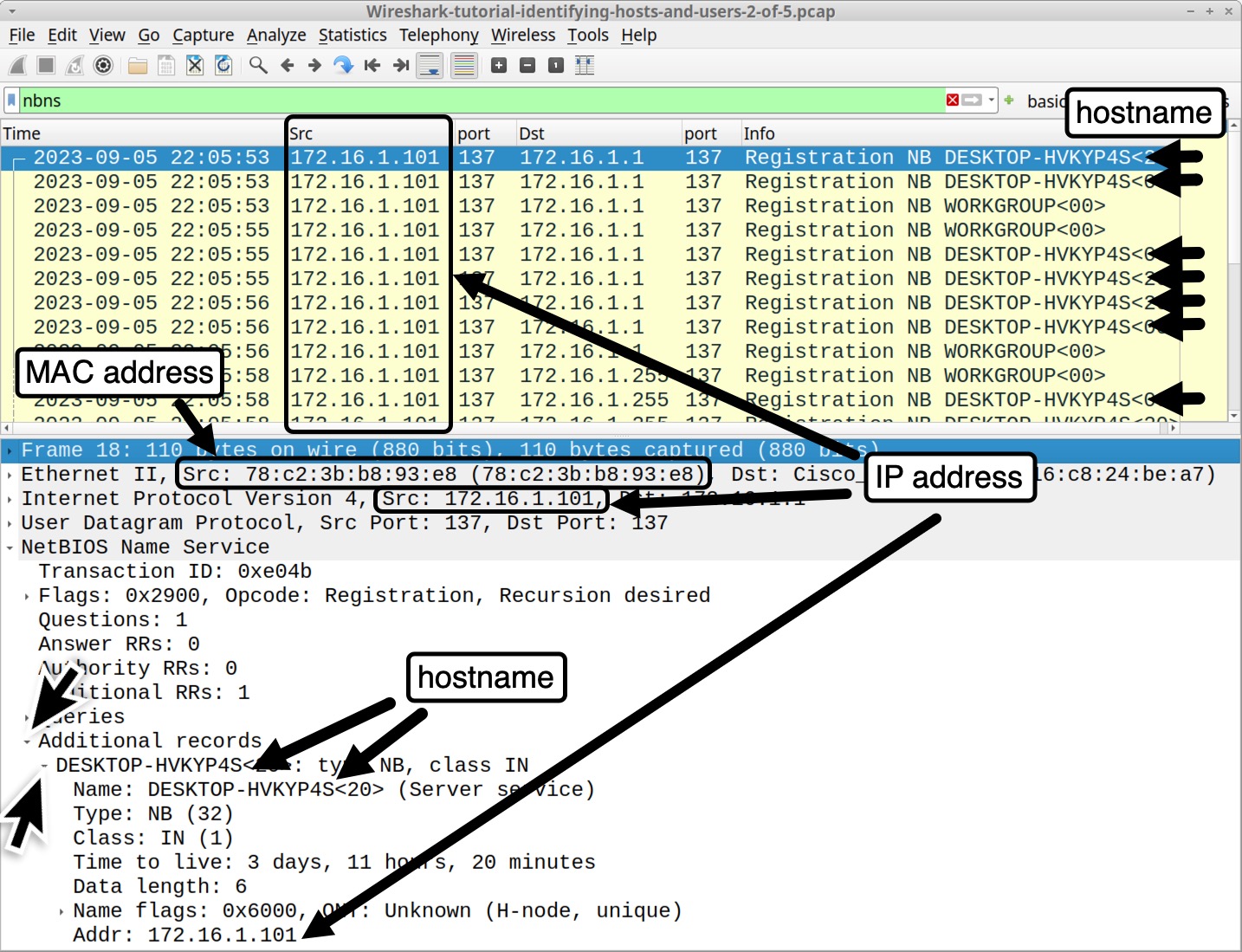
Getting started:
Install Wireshark and open it. (Pro tip: Run it with admin privileges for full access - “sudo”.)
Choose the network interface to capture traffic (e.g., your Wi-Fi adapter).
Use filters to focus on specific traffic, like
http,tcp.port==80, orip.addr==192.168.1.1.
Fun command:
tcp.flags.syn==1 && tcp.flags.ack==0– This filter captures SYN packets, perfect for spotting suspicious port scans.\>
tcp.flags.syn==1: This condition filters packets where the SYN flag is set. This flag is used during the initial handshake process in TCP to indicate a connection request.\>
tcp.flags.ack==0: This condition filters packets where the ACK flag is not set. This indicates that the packet is not acknowledging any data.
Advanced Insight: Dive into protocol-specific analysis. For example, use the Follow TCP Stream feature to reconstruct conversations or extract credentials from plaintext traffic like HTTP. Pair Wireshark with tools like tshark for scripting and automation.
Case Study: A network administrator once used Wireshark to detect a data exfiltration attempt in real-time. By applying a filter for large file transfers (tcp.len > 1000), they pinpointed an internal device communicating with an unknown server overseas. The device was isolated, and a breach was averted.
Explore Wireshark further by visiting this URL: https://www.kali.org/tools/wireshark/
2. Nmap: The Cybersecurity Swiss Army Knife
What it does: Nmap is a versatile tool for network discovery and security auditing. It identifies devices, open ports, and running services on a network, and detects operating systems and software versions. Nmap is crucial for network inventories, service management, and monitoring uptime. It also helps find network vulnerabilities, making it essential for maintaining network security. Its efficiency in scanning large networks and providing detailed configurations makes it popular among cybersecurity experts.
Why it’s awesome: Nmap is an incredibly powerful tool that can handle everything from scanning your local network for open ports to mapping out a large corporate network. It does all of this efficiently and effectively, making it a favorite among both cybersecurity professionals and hackers. Its versatility allows it to serve both offensive and defensive purposes, making it a true double agent in the world of network security.
![Nmap Commands | How to Use Nmap Tool [Nmap Cheat Sheet]](https://techofide.com/media/uploads/2021/07/01/nmap-fast-scan.webp)
Getting started:
Basic scan:
nmap 192.168.1.1Scan for open ports:
nmap -p 1-65535 192.168.1.1Detect services and versions:
nmap -sV 192.168.1.1nmap -F scanme.nmap.org: This command scans the most common 100 TCP ports on thescanme.nmap.orghost to detect open ports and associated services.The
-Foption in the command instructs Nmap to perform a fast scan, limiting the scan to the 100 most common TCP ports instead of scanning all 65,535 possible TCP/UDP ports, thereby saving time and resources. The target host in this command isscanme.nmap.org, a specific domain maintained by the Nmap project for users to test their Nmap commands and experiment with network scanning techniques.
Pro tip: Use --script to leverage Nmap’s scripting engine for advanced tasks. For example:
nmap --script vuln 192.168.1.1runs vulnerability scans.
Advanced Insight: Create custom scripts using Nmap’s NSE (Nmap Scripting Engine) to automate checks for specific vulnerabilities. For instance, write a script to detect outdated TLS protocols across a range of servers.
Case Study: During a routine scan of a company’s intranet, an IT team discovered an exposed database using Nmap. The database had no authentication configured and contained sensitive customer data. With this discovery, they secured the database and avoided a potential breach.
Explore Nmap further by visiting this URL: https://www.kali.org/tools/nmap/
3. Metasploit Framework: The Ethical Hacker’s Playground
What it does: Metasploit is a comprehensive tool used for penetration testing, which involves assessing the security of systems by simulating attacks. It allows security professionals to identify and exploit vulnerabilities in networks and applications, helping them understand how an attacker might gain unauthorized access. By doing so, it aids in evaluating the effectiveness of security controls and identifying areas that need improvement.
Why it’s awesome: Metasploit is highly valued because it simplifies the process of testing system vulnerabilities. It provides a vast library of exploits and payloads, making it easier to simulate real-world attacks. This automation enables security experts to quickly identify weaknesses in a system without manually writing exploit code. As a result, they can spend more time focusing on analyzing the results and implementing necessary security measures to protect against potential threats.
Getting started:
Launch the framework:
msfconsoleSearch for an exploit:
search exploit smbUse an exploit:
use exploit/windows/smb/ms17_010_eternalblueSet parameters and payloads:
set RHOST 192.168.1.10Run the exploit:
exploit
Advanced Insight: For a more user-friendly experience, integrate Metasploit with Armitage, which provides a graphical user interface (GUI) that simplifies the process of managing and executing exploits. This integration allows security professionals to visually map out their attack strategies and streamline their workflow. Additionally, you can script advanced post-exploitation techniques using Meterpreter scripts, which are powerful tools within Metasploit. These scripts can automate complex tasks such as privilege escalation, where you gain higher-level access to a system, and persistence, where you ensure continued access even after a system reboot.
Case Study: In a real-world scenario, a penetration tester employed Metasploit to uncover a critical SQL injection vulnerability in a client's web application. This vulnerability allowed the tester to gain unauthorized access to the application's database, demonstrating the potential for data breaches. By exploiting this flaw, the tester was able to extract sensitive information and showcase the significant risk posed by inadequate input validation. This case highlighted the urgent need for the client to implement stricter input validation measures to protect against such vulnerabilities and safeguard their data.
Explore Metasploit further by visiting this URL: https://www.kali.org/tools/metasploit-framework/
4. Burp Suite Community Edition: The Web App Gladiator
What it does: Burp Suite is a comprehensive tool designed for testing the security of web applications. It allows security professionals to identify and exploit vulnerabilities within web applications, ensuring robust protection against potential threats.
Why it’s awesome: Burp Suite excels in its ability to intercept and analyze HTTP requests, providing deep insights into the data exchanged between a client and server. It also automates vulnerability scanning, making it easier to detect issues like SQL injection, cross-site scripting, and more. The Community Edition, which is free, offers a wealth of features to help beginners and seasoned professionals alike start securing web applications effectively. Its intuitive interface and powerful capabilities make it an indispensable tool in the arsenal of any web security expert.

Getting started:
Set up Burp as a proxy in your browser.
Use the intercept tab to analyze and modify HTTP requests in real-time.
Scan web apps for vulnerabilities like XSS and SQL injection.
Pro tip: Pair Burp with your favorite browser plugins like “FoxyProxy” to streamline your workflow.
Advanced Insight: Leverage Burp Suite’s API to develop custom extensions that automate repetitive tasks. For example, you can create an extension to automatically fuzz input fields using a predefined wordlist, enhancing efficiency and thoroughness in testing.
Case Study: A security consultant utilized Burp Suite to intercept and examine traffic from a mobile application. During this process, they identified sensitive data being sent in plaintext. This discovery prompted the app developers to implement encryption for all communications, significantly improving the app's security posture.
Explore Metasploit further by visiting this URL: https://www.kali.org/tools/burpsuite/
5. John the Ripper: Passwords Beware
What it does: John the Ripper (JtR) is a powerful tool designed to crack passwords by identifying weak password hashes and recovering plaintext passwords from them.
Why it’s awesome: John the Ripper stands out due to its speed and flexibility. It is highly customizable, allowing users to tailor its functionality to specific needs. It supports a wide range of hashing algorithms, making it versatile for various security assessments. Whether you're dealing with simple MD5 hashes or more complex bcrypt hashes, JtR can handle them efficiently. Its ability to quickly crack hashed passwords makes it an essential tool for security professionals who need to assess the strength of password policies and ensure the protection of sensitive data.

Getting started:
Use wordlists like
rockyou.txtfor dictionary attacks.Crack an MD5 hash:
john --wordlist=rockyou.txt --format=raw-md5 hash.txt
Here I used of the john command with the --single mode and the --format=raw-sha256 option to crack passwords from the file topgun_hashes.txt. This file contains 4 password hashes in the Raw-SHA256 format, and John the Ripper is attempting to crack them using username-based rules applied by the --single mode. A warning is displayed about poor OpenMP scalability, with a suggestion to use --fork=2 for improved performance. The tool successfully cracks the passwords, revealing variations like "Topgun", "ToPGun", and "topGun". The session completes, and it suggests using the --show option to reliably display all cracked passwords.
Advanced trick: Combine rules and hybrid attacks for more effective cracking:
john --wordlist=rockyou.txt --rules --format=raw-md5 hash.txt
Advanced Insight: To significantly enhance password cracking speed, explore GPU acceleration with tools like Hashcat. By combining Hashcat's GPU capabilities with John the Ripper, you can tackle complex brute-force scenarios more efficiently. This approach leverages the parallel processing power of GPUs, drastically reducing the time required to crack even the most challenging password hashes.
Case Study: In a recent security assessment for a large corporation, the security team employed John the Ripper to evaluate the strength of their password storage mechanisms. They discovered that an admin password was stored using a weak hashing algorithm, which JtR cracked in under an hour. This finding was a wake-up call for the organization, prompting them to implement stronger password policies and adopt more secure hashing algorithms like bcrypt or Argon2. This proactive measure not only fortified their security posture but also safeguarded sensitive administrative access from potential breaches.
Explore JtR further by visiting this URL: https://www.kali.org/tools/john/
6. Autopsy: CSI for Cybersecurity
What it does: Autopsy is a powerful digital forensics tool designed to analyze disk images and uncover critical evidence during investigations.
Why it’s awesome: Autopsy stands out due to its user-friendly graphical interface, which makes it easier to perform complex forensic tasks. It allows investigators to efficiently recover deleted files, analyze browser history, and extract other vital data. This accessibility and functionality make it an essential tool for both novice and experienced forensic analysts.
Getting started:
Open a disk image in Autopsy.
Use modules like “File Analysis” or “Timeline” to explore data.
Export reports for evidence.
Advanced Insight: To enhance your forensic investigations, pair Autopsy with command-line tools like Sleuth Kit. This combination allows you to perform advanced operations, such as carving through unallocated disk space to uncover hidden files that might not be visible through standard analysis. This capability is crucial for uncovering deeply buried evidence that could be pivotal in an investigation.
Case Study: In a notable fraud investigation, an investigator utilized Autopsy to recover deleted emails from a suspect’s hard drive. These emails contained incriminating information that was crucial to the case. By meticulously analyzing the recovered data, the investigator was able to piece together a timeline of fraudulent activities, which ultimately provided the evidence needed to secure a conviction. This case highlights the power of Autopsy in uncovering digital evidence that can make or break a case.
Explore Autopsy further by visiting this URL: https://www.kali.org/tools/autopsy/
Final Thoughts
Each of these tools is a powerhouse in its own right, whether you're sniffing packets, scanning ports, cracking passwords, or hunting for vulnerabilities. Imagine the possibilities as you dive into the world of cybersecurity, armed with these powerful yet accessible tools. They are free, beginner-friendly, and incredibly useful, making them perfect for anyone eager to explore the digital landscape. Start small, experiment, and let these tools unlock your inner cybersecurity wizard. Embrace the journey of learning and discovery, and watch as your skills grow and evolve.
But remember, with great power comes great responsibility. Use your newfound abilities wisely and ethically. Don't be the person who uses Nmap to poke at your neighbor’s Wi-Fi; respect privacy and legality. Instead, focus on building a safer digital world for everyone.
Happy hacking – ethically, of course!


